Pentesting
Pentesting for higher cybersecurity
Hacker attacks are especially risky when sensitive information and data are involved. In pentests, we consciously search for security vulnerabilities in IT systems before hackers identify and exploit them.
The goal of pentesting is to identify these gaps at an early stage and thus develop quick solutions.
Be safe with pentesting
The number of cyber attacks has been rising for years. This is why the German Federal Office for Information Security (BSI) also recommends pentestingto check the current security of IT systems. It is important that the tests are scheduled on a regular basis.
This is how we run pentests
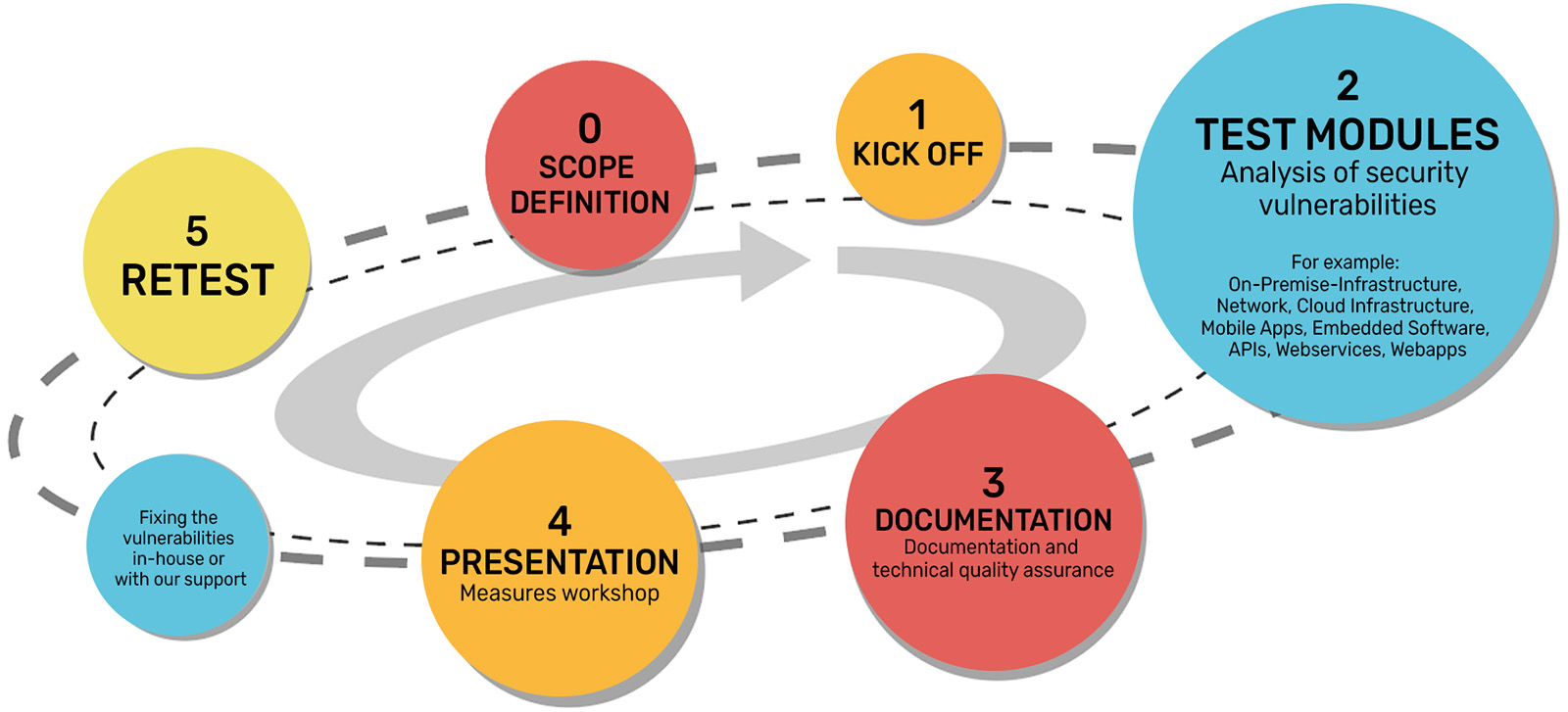
We use a combination of automated tests and manual, explorative procedures. We combine the speed, repeatability and high throughput of automated testing with the creativity, expertise and combinatorial skills of our cybersecurity engineers.
Meanwhile, we draw on known databases/repositories such as NVD (National Vulnerability Database) of the U.S. government or CVE (Common Vulnerabilities and Exposures) U.S. Department of Homeland Security, to identify possible vulnerabilities. With our many years of experience in the field of software development to the highest IT security standards, we design test and attack scenarios tailored to your software. This allows us to check possible attack vectors (one attack path) or attack surfaces (multi-stage attack methods).
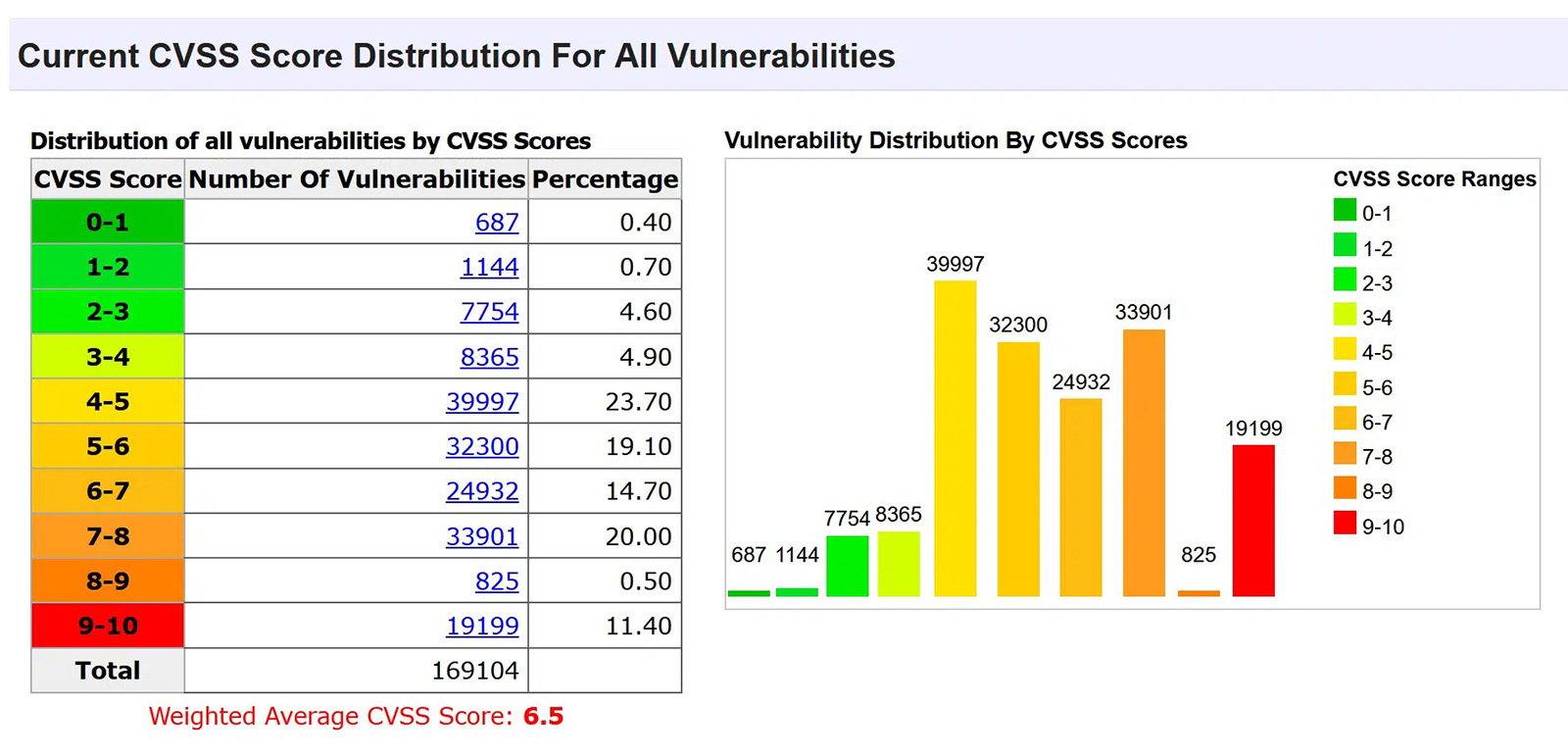
As a result, every vulnerability found is evaluated using the Common Vulnerability Scoring System (CVSSv3) and provided with possible mitigation measures, including the degree of effectiveness.
In other words, you get a quick overview of the security status of your software and can use this to improve it.
We check the corresponding applications (Web/WebApps/Apps) for security risks during our pentests. This sometimes includes front-end and back-end, but also web services, APIs and other components.
These are the vulnerabilities we test for you
Synergies are our recipe for success
BAYOOTEC and BAYOOMED – Many years of experience in software development, not least in safety-critical areas, and IT security meet expertise in the field of medical software. With this cooperation we support you with the comprehensive knowledge of both organizations. Write us and we will be happy to advise you and talk about the possibilities for more security of your software, medical software, apps and DiGA.
Get in touch now
Whether you have a specific software project in mind or you are looking for answers to open questions – we are here to help you.
Arrange a non-binding appointment here.